Absolutely perfect. I was traveling with a friend and we decided to watch a movie I had on my hard drive. Once I booted into i3 and I had to use a couple key chords to navigate, they said, “Your computer gives me anxiety.” 😂
Same person almost shit their pants when I replaced
youtu.bewithyewtu.bein a URL to get a region locked video to play. I am a bonafide hacker in their eyes.My idiot brother, who fancies himself a tech guru… because he reads the
newsmarketing around the tech specs of new console releases every couple of years…Legitimately thought I was hacking into our own ISP when I opened a terminal infront of him to configure a VPN setting that didn’t yet have an option to do so in the GUI.
Lile he tried to have an ‘intervention’ with me over it.
For … running a few commands to check my existing and active network interfaces, then glancing at a webpage and starting the vpn process with an extra flag or two.
I was completely unable to convince him that I hadn’t done anything even remotely close to like pen-testing the local DNS server… which is what he… seemed? to think I was doing?
Gotta love incredibly overconfident + incompetent people.
…
I have also had people at cellphone shops either get angry at me for mentioning outloud, or try to hide the fact that you can plug a phone with a broken screen into a usb hub, and then their own keyboard, monitor and mouse, in certain situations, and be able to log in to the phone to do inane parts of their recovery or migration processes … when your screen is borked, but the phone itself is still functional.
I had employee guy laugh at the notion this would work, another guy say sure you can try it, and then got angry that it worked, and another act like I was performing some kind of dark magic that the other customers in the store could not be allowed to know about.
…
EDIT: Oh I forgot to mention the abominable absurdity of my brother trying to give me an ‘intervention’ over anything, at all, ever.
See, while I was
studying the bladegetting two simultaneous bachelors degrees from the best Uni in the state, he was going to raves, giving himself serotonin shock syndrome, all while functionally being homeless.Multiple times in my life I have had to drop everything I was doing and prevent him from carrying out a very credible suicide threat, or save him from ODing.
Myself on the other hand, … uh, no nothing like that, and I’d not even given him an ‘intervention’ after saving him from an OD or two.
Anyway, I’m fairly sure I could drive him back to drug use if I somehow forced him to learn how some of the R code I used and wrote for statistical analysis actually works, or the same for any of the insane spider webs of 200, 300 line custom, one-off SQL queries I often had to write in various data analyst positions before they let me restructure their DBs a bit into something less insane.
His “intervention” reminded me of this old sketch. Thought you might appreciate!
You know, I hadn’t seen that sketch before…
… but another thing that my idiot brother did, which was actually the final straw between me and my entire family:
My doctors, over the year prior, with me seeing them fairly frequently, running a good deal of blood work tests on me … well they decided to change up my medication somewhat, take me off of one drug, replace it with another…
… because that drug they were taking me off of was causing me to … not quite develop actual diabetes, but develop many signs of pre-diabetes… and they had figured out a way to switch me over to a set of drugs where that would not be a problem.
My brother interpreted this as me making up all of what I just said whole cloth, as if i was delusional and insane, despite me literally showing him the blood test results, annotated by the metabolic expert, and the new medication plan from other doctors.
So we got into an argument, the next day my entire immediate family has decided that I need to be institutionalized, in a mental asylum in the middle of fucking nowhere, fuck my career I guess? I was making almost twice as much as my brother and probably more than my dad at the time.
I just moved out while my brother was at work, never looked back.
Damn, seems I unlocked a core memory. Condolences. Thanks for sharing though! Quite the story…
Ah, this one was fairly recent, and I have more recently been diagnosed with ©PTSD from… how often insane shit like that has happened to me.
But, typing it out is… better than just stuffing it down… 6 months ago, typing out a similar story would have filled me with rage, all muscles clenching… this time I only grit my teeth once.
Progress.
… I appreciate the condolences though.
… Spent a long, long time being gaslit, its … helpful for me to type it out, and not be blamed for it.
Glad to help!
Yeesh. I relate fully to the brother part. Mine also likes to pretend, but at least isn’t that oblivious about the terminal. Intervention, though?! LMAO
“Friends don’t let friends Gentoo”, or something
He has an extremely thin skin, a massive inferiority complex, somehow has worse social skills than myself, despite me being autistic and him not… I could go on, but I already added more in an edit to my above post.
So anyway I went no contact with my entire dysfunctional family (they’re all this magnitude of nuts but in their own special ways) years ago rofl, my mental health has never been better.
I was installing Alpine Linux on a Raspberry Pi 5 and was using the kitchen TV as a temporary monitor. My parents thought I was sending encrypted messages. I was just updating the repository list to find the quickest mirror.
It’s funny to me how some people see text scrolling by on a screen and immediately think witchcraft.
I used to do something similar when I was working in embedded systems, specifically because my superiors had no idea. I would just put our OS up to compile on repeat so one if my machines was always spitting out nonsense (but vaguely related to work).
“Sorry boss, just waiting on the new build to finish up so I can start on that.”
Used to keep a terminal sesh up that was just scrolling
topon the dev server whenever I felt like being lazy while looking productive. Took my very tech savvy boss a couple months before he finally noticed.I’m pretty sure the VP of engineering knew what I was up to, but I think he also understood that I didn’t get paid enough to be as neurotic as he was and I generally got stuff done ahead of schedule any way.
Hollywood fucked over everyone
Ok, so I happen to be the paragon of security through obscurity.
- Linux
- Sway
- Dvorak layout
- Mechanical keyboard c̄ blank keycaps
Come at me bruh
The last 2 can be mitigated by just plugging in a different keyboard, the second one by just pulling the drive, the first doesn’t really need mitigation, but nothing a $5 wrench won’t solve.
This guy xkcds:
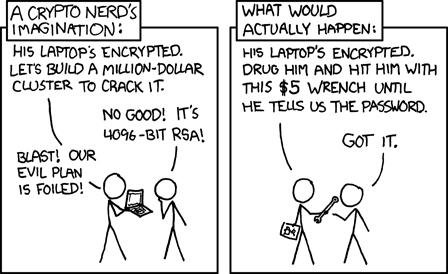
gets hit with wrench
cums “h-harder daddy~”
“well shit, now wtf do we do?”
“if you don’t give the password I’m gonna stop” 🤷♂️
“B-but I’m into orgasm denial too” 🥺
After that point, you don’t want to know what is in the laptop anyway
But, that’s also when morbid curiosity kicks in~
“h-harder daddy~”
That was the exact password.
You can stop now
The key map tends to apply to all keyboards.
Depends on your keyboard. I have the kind where you can quick switch with a key combination.
I guess it’s possible for the keyboard itself to handle that, but I’ve set that up in the OS on both windows and Linux machines. And when I replaced a shitty keyboard with a better one just a little while ago, it had Dvorak already as the default layout.
Yeah of course. That’s how I did it when I tried Dvorak a couple of years ago too. Just mentioning that stuff is possible today.
“My $5 wrench says you better start installing Windows.”
“Sure thing, just let me wipe the drive in the process…”
Keymap isn’t going to change automatically by plugging in a new keyboard…
Apparently I am too…
- Linux (NixOS BTW)
- Also Sway
- Colemak
- Mechanical keyboard, but the key caps are still QWERTY.
Linux+i3+emacs+dvorak+querty_mech_kbd
damn it. I am “one of those dudes”
My keycaps are Morse code
Switching to Dvorak caused the gratifying result of people that would just start trying to use your keyboard without being absolutely befuddled.
I used my own modified colemak layout for some time.
Hey, me too!
Joke aside, it’ll only work implying that they have to use the same computer. Anyone tech savvy enough will know that it’s trivial to put an unencrypted drive in another machine and read it.
The computing equivalent of a stick shift.
If only you could start it with a dead battery!
Wouldn’t that be something that makes you manually tile your windows? Or are you making fun of i3 for not properly placing tiling windows to split the active one in half along the longer side?
Bonus points: use non-qwerty keyboard for added obfuscation (but keep the qwerty key caps of course).
As I’m French, I do the contrary: international QWERTY layout on AZERTY physical keyboard. I want to switch to an ergonomic layout like ergo-l though, but it’s hard to learn.
I love this. I just wish we could use a different meme format, I am tired of seeing that dudes face.
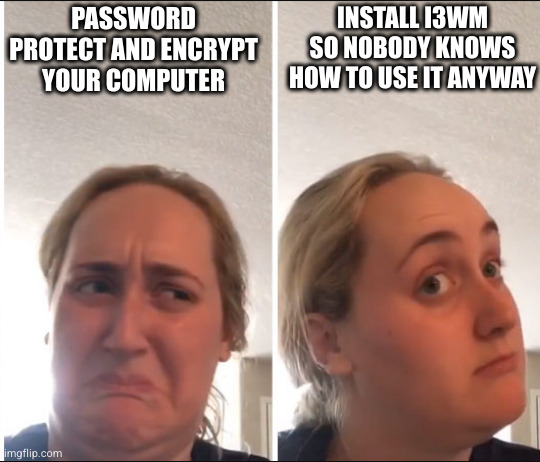
Hero

I love but it!
I agree. There are so many available now.
Fixed the image for you

Ah thanks man, could you add some left/right padding as well?
Yeah, no problem

the real fix would have been the removal of drake

Only encrypt your sensitive data.
This is like me when I try to use my wife’s iPhone. Where are the buttons? How do I exit the app?
When in doubt, swipe up
try finger but edge
(my android phones don’t have buttons and haven’t for years)
multi step authentication flows that are customizable for each user would be kinda cool if that doesn’t exist already.
not too crazy like two factor authentication, just patterns or puzzles to arrange in different ways.
so every time someone tries to access an account, the authentication process is different every time
It opens up a page of my handwriting and it must be translated in order to unlock the computer. Even the most powerful linguist in the world couldn’t crack it.
delightfully horrifying
I love sway :3
Sway is fine. I still prefer i3 because I still use many X applications.
Now for this meme specifically, sway and i3wm are actually easy to understand once you know the basic key chords. Sway in particular can also allow drag and drop to tile manually without shortcuts.
Dwm though is a nightmare for Linux beginners let alone those who never use Linux before. I3 needs a .config file, so newbies can read it and figure out the key bindings. On Dwm? It doesnt need one because the system can just run the compiled dwm executable. So if you really want to make it more secure: configure dwm to your likings => compile it => delete the source folder. Nobody will know wtf is going on, except you.
i3 can also drag and drop to tile, iirc.
Riverwm for the win
dwm suckless zen gentoo gigatron trilonaire elonmusknuker arm for the win
I was an i3 and sway user but I lapsed to the dark side.
I tried KDE with Krohnkite tilling extension on a new laptop and liked it way too much. It’s slowly becoming my main DE.
It’s configured with i3 shortcuts of course, so there’s that.
I’ve been wanting to do that
(i3 user here with dynamic composition of config file based on content of my “dotfiles” repo acroos my devices, and deciding some parts of it (like screen config) by the localhost name).
Can you tell me more about your experience? KDE ds indeed sexy. Calibre, okular and kde-connect sure are).
Well that was my main motivation to try KDE, everything is working fine out of the box and is highly configurable/rice-able.
It just needed that tiling wm love. So far I have nothing really bad to say about this configuration. You can have a very i3 feeling by adding gaps, rounded corners, removing title bars, have transparency or blur etc. Or you can do a mix of both worlds to make it easier for the rest of your household (example, having title bars makes the windows movable by mouse. I kept them for my significant other, she hates not being able to choose the windows size but it makes it easier for her to watch YouTube…)
Keyboard shortcuts are configured in kde settings, so there will be conflicts at first between “normal kde” binds and tilling plugin binds, but nothing impossible to change.
I haven’t seen any bugs, my dual screen is working great. I have yet to finish my personalization but I’m at about 80% and it as become my daily driver for working.
I am not certain about your different config by localhost as I now sync the dotfiles and packages across the two pc (laptop + mini pc) which are the same hardware and so, exact same look and feels. When not in laptop mode they share the same dual screens so it makes sense to me.
The only downside I see is that it relies on a community GitHub. The one I linked is the only one I found to be updated. There are plenty of forks or similar projects not updated since 2022.
So unless KDE officially does it one day (and does it well), we have to use community plugins and hope that they stay updated.
Mandatory over compressed screenshot (in night theme and night light cause, well it’s still night… It will transition everything to day at sunrise)
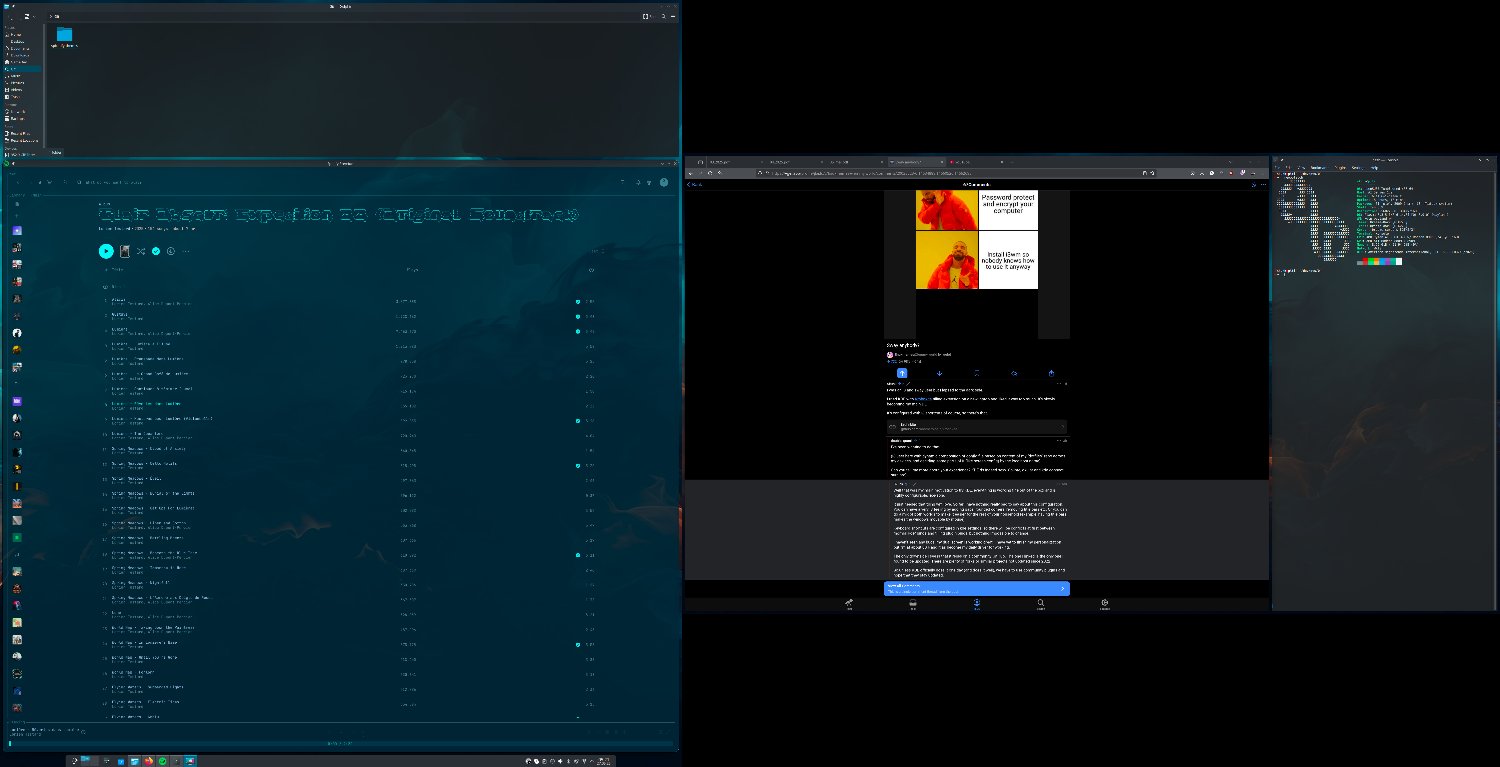
So, just with the keyboard, can you:
- move focus across windows
- move windows
- resize windows
- run any program?
Also, do you have the “tabs, stack, columns, rows” layouts?
Yes to all. Programs are run from whatever launcher you want to use, default KDE or another one.
Default Key Bindings
Key Action Meta + . Focus Next Meta + , Focus Previous Meta + J Focus Down Meta + K Focus Up Meta + H Focus Left Meta + L Focus Right Meta + Shift + J Move Down/Next Meta + Shift + K Move Up/Previous Meta + Shift + H Move Left Meta + Shift + L Move Right Meta + I Increase Meta + D Decrease Meta + F Toggle Floating Meta + \ Next Layout Meta + | Previous Layout Meta + Return Set as Master Meta + T Use Tile Layout Meta + M Use Monocle Layout unbound Use Spread Layout unbound Use Stair Layout Nice! I’ll try it, then














